A Useful Band-Aid For Sites Still Using SMS for Logins
This entry describes how use a free Google Voice VOIP number to receive SMS login codes for websites that don't support Authenticator apps or hardware keys for 2FA.
If you have any doubts that using your mobile phone to receive an SMS code to login to your favorite websites is insecure, ask the 40 people who lost millions in cryptocurrency to a single 20 year old college student. Or get some 🍿 and watch a 2 minute excerpt from this video:
There are two major weaknesses of SMS login codes for authentication.
- SMS is an unencrypted and insecure protocol allowing for various protocol level attacks by mildly determined attackers.
- Mobile service providers have yet to identify an effective way of preventing attackers from visiting a store or calling a customer service rep and, by using social engineering, convincing them to transfer your current mobile phone number attached to the SIM card in your phone to the SIM card of the burner phone in the hands of the attacker. This is known as a SIM Swap/Port Out Attack
Once an attacker accomplishes #2, they are far more likely to be able to break into one of your accounts as they will be now be receiving all the SMS login codes used to login to your bank, government, health, and yes, million dollar bitcoin accounts. For sites that solely use an SMS code sent to your mobile phone, you are totally 💩 out of luck. If an attacker manages to SIM swap an Uber rider account? Free rides and UberEats. If the attacker SIM swaps an Uber driver account? An entire week's worth of earnings drained.
How do we overcome this predicament?
- Use a better alternative for 2FA such as authenticator apps (i.e. Google Authenticator) and hardware keys (e.g. Yubico).
- Require a PIN on your mobile phone account to help prevent SIM swaps
These are great first steps, however:
- There is not a working quorum of popular online sites that use #1 (for example my bank only provides 2nd factor via SMS login codes)
- An attacker can still socially engineer their way around #2; they will just keep trying until they get an employee that gives into a little sweet talking.
This is where we take advantage of the lack of customer service we typically complain about with internet companies; Google Voice has no easily accessible humans to authorize port-outs.
The only person that can authorize a port-out is you; specifically 'you' logged into your Google account. So if you have your main accounts on lock 🔒, using Google Voice (or any other VOIP service that can receive texts/calls) is nice defense against socially engineered SIM swaps.
For those not familiar with Google Voice:
- it is free
- provides you a number to make and receive calls and texts
- can be used with an existing google account, or if you don't use google, create a dummy google account with the sole purpose of using Google Voice for SMS
Once you create a Google Voice account, download the Google Voice app to your mobile phone. Make sure to avoid transferring you Google Voice number to your actual mobile device number and avoid forwarding texts/calls to your mobile number (this would defeat the purpose of avoiding your main mobile number being vulnerable to SIM swaps). Here are recommended settings for Google Voice:
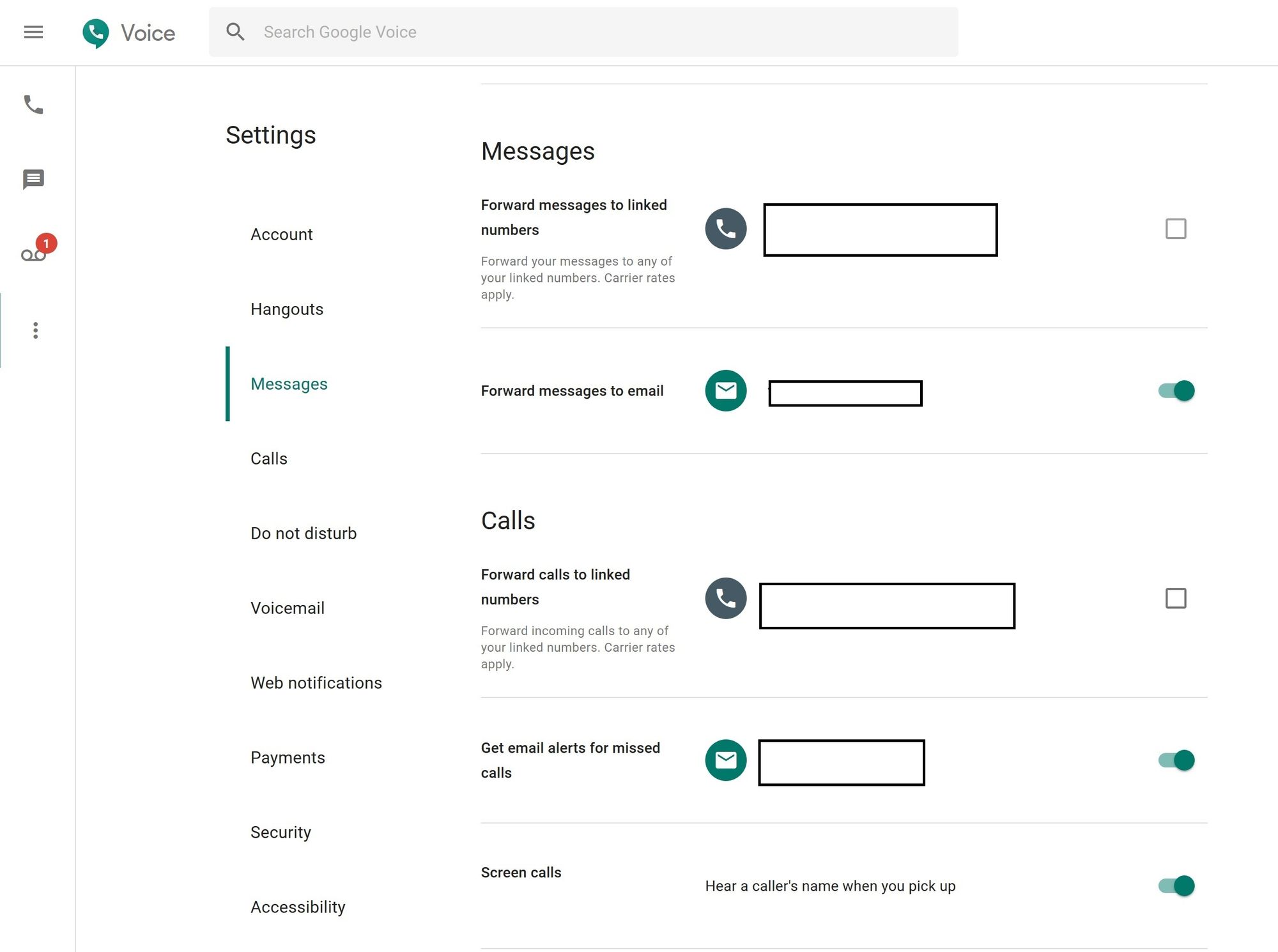
Now armed with your new Google Voice number,
- for any website that still insists on using SMS codes, use your Google Voice number instead�.
- before removing your existing mobile phone number make sure to enroll and verify your Google Voice number works for SMS login codes. Some websites don't play well delivering SMS codes to VOIP numbers, and if this is the case, you will have to stick with your standard mobile phone until the site supports proper authenticator apps or hardware based keys.
- once your Google Voice number is enrolled successfully, you should completely remove your current mobile phone number as an option for receiving SMS login codes. If an attacker compromises your password for that website����, they may be able to designate any secondary mobile phone numbers on the account to receive SMS codes.
Rinse and repeat the above for all your important financial, health, government, email, data backup, and money related accounts that still rely on SMS login codes. I also use the above approach for sites that don't allow both a hardware key and authenticator app. For example, my Google account is secured by my choice of a Google Authenticator code or my Yubikey hardware key. I disabled the option to login via SMS codes for my Google account because I already have a fallback if my Google Authenticator app is inaccessible (e.g. my phone fails or is stolen) with my Yubikey. However if a site only supports Google Authenticator, I will use SMS codes sent to my Google Voice number as a fallback (e.g. Instagram).
Remember this band-aid is a temporary necessity. Over the next few years I expect the 'long tail' of major websites to migrate away from SMS based 2FA.
